How To Open Computer Configuration In Windows Server 2016

In that location are some uncomplicated Group Policy Settings, which if appropriately configured, tin can help to prevent data breaches. You can make your organizational network safer by configuring the security and operational behavior of computers through Grouping Policy (a group of settings in the computer registry). Through Group Policy, you can prevent users from accessing specific resources, run scripts, and perform simple tasks such as forcing a particular home page to open up for every user in the network.
Important Group Policy Settings to Forestall Breaches
Here is the list of meridian 10 Group Policy Settings:
- Moderating Access to Control Panel
- Prevent Windows from Storing LAN Manager Hash
- Control Access to Control Prompt
- Disable Forced Organisation Restarts
- Disallow Removable Media Drives, DVDs, CDs, and Floppy Drives
- Restrict Software Installations
- Disable Guest Business relationship
- Set Minimum Password Length to Higher Limits
- Set Maximum Password Historic period to Lower Limits
- Disable Anonymous SID Enumeration
In this article, you will larn why these Grouping Policy settings but cannot be ignored.
1. Moderating Admission to Control Console
Setting limits on a computers' Control Panel creates a safer business organization environment. Through Command Console, you lot can command all aspects of your computer. So, by moderating who has access to the computer, y'all tin can keep data and other resources safe. Perform the following steps:
- In Grouping Policy Direction Editor (opened for a user-created GPO), navigate to "User Configuration" "Administrative Templates" "Control Panel".
- In the correct pane, double-click "Prohibit access to Control Console and PC settings" policy in to open up its properties.
- Select "Enabled" from the three options.
- Click "Employ" and "OK".
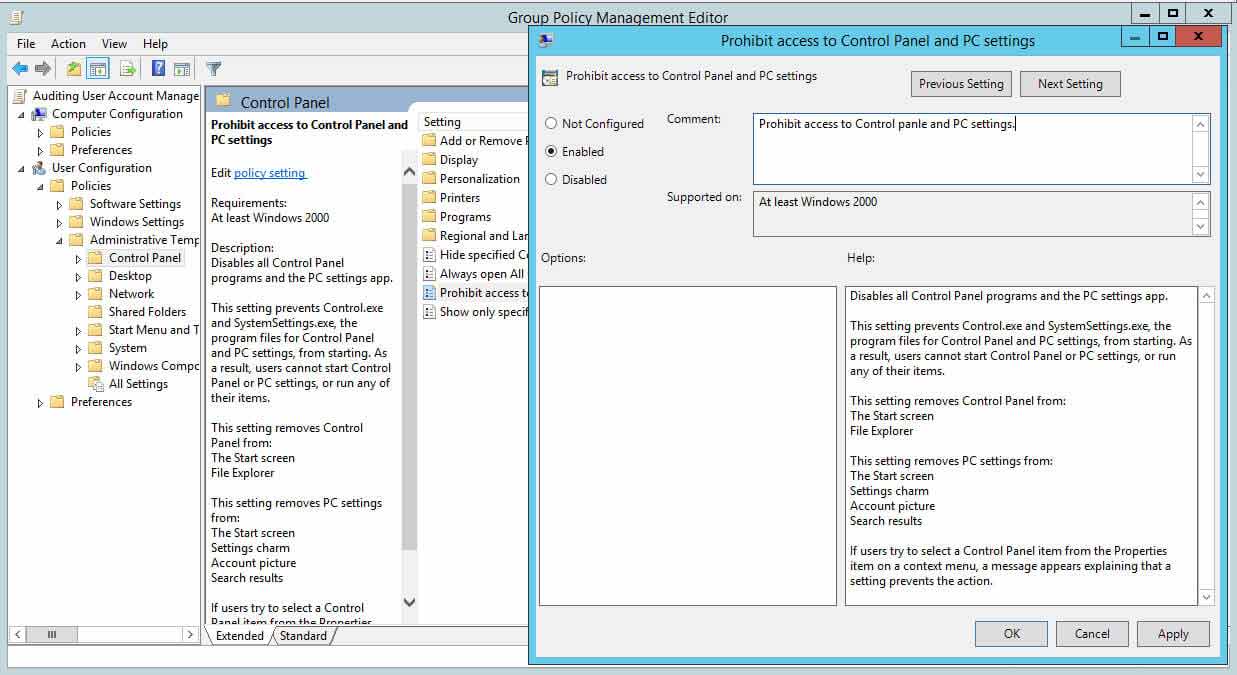 Figure 1: Configuring Control panel settings through GPO
Figure 1: Configuring Control panel settings through GPO
two. Foreclose Windows from Storing LAN Manager Hash
Windows generates and stores user account passwords in "hashes." Windows generates both a LAN Director hash (LM hash) and a Windows NT hash (NT hash) of passwords. It stores them in the local Security Accounts Manager (SAM) database or Agile Directory.
The LM hash is weak and decumbent to hacking. Therefore, yous should prevent Windows from storing an LM hash of your passwords. Perform the following steps to practice so:
- In Group Policy Management Editor window (opened for a custom GPO), go to "Figurer Configuration" "Windows Settings" "Security Settings" "Local Policies" "Security Options".
- In the correct pane, double-click "Network security: Do non store LAN Manager hash value on adjacent password modify" policy.
- Select "Define this policy setting" checkbox and click "Enabled.
- Click "Utilize" and "OK".
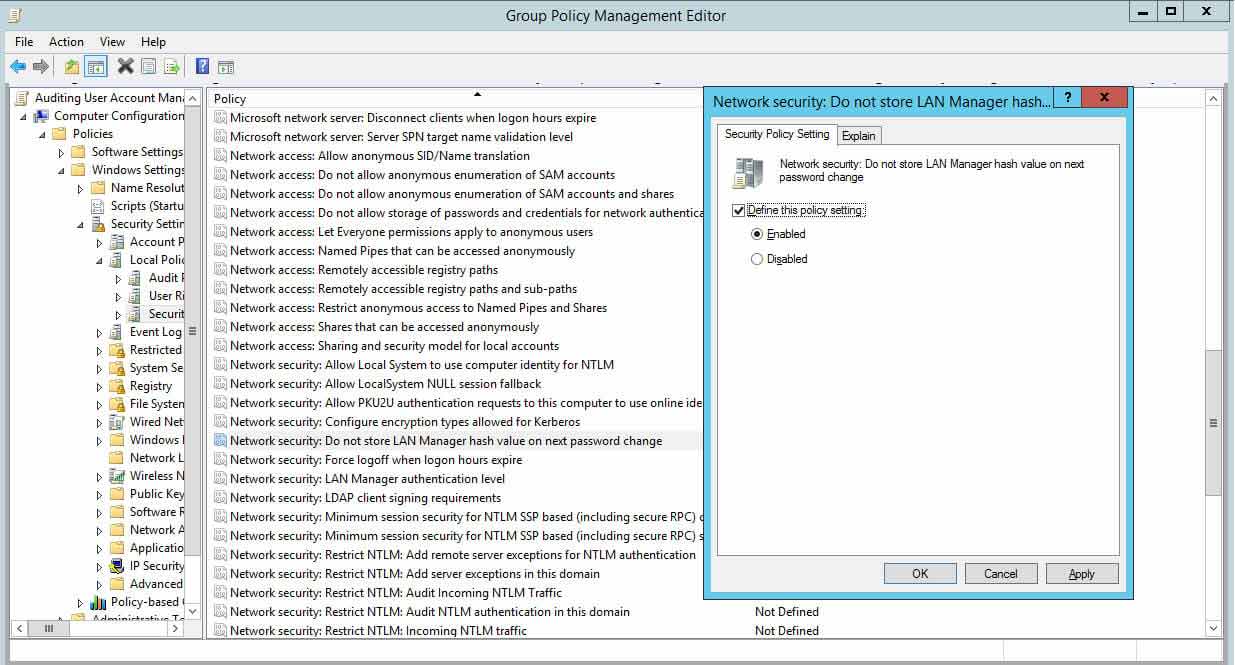 Effigy two: Configuring policy to not store LAN Director hash value policy
Effigy two: Configuring policy to not store LAN Director hash value policy
iii. Control Access to Control Prompt
Control Prompts tin can be used to run commands that give loftier-level access to users and evade other restrictions on the system. And then, to ensure system resources' security, it'south wise to disable Control Prompt.
After you accept disabled Command Prompt and someone tries to open up a command window, the system will display a message stating that some settings are preventing this action. Perform the following steps:
- In the window of Group Policy Management Editor (opened for a custom GPO), become to "User Configuration" "Windows Settings" "Policies" "Administrative Templates" "System".
- In the right pane, double-click "Prevent access to the command prompt" policy.
- Click "Enabled" to apply the policy.
- Click "Utilise" and "OK".
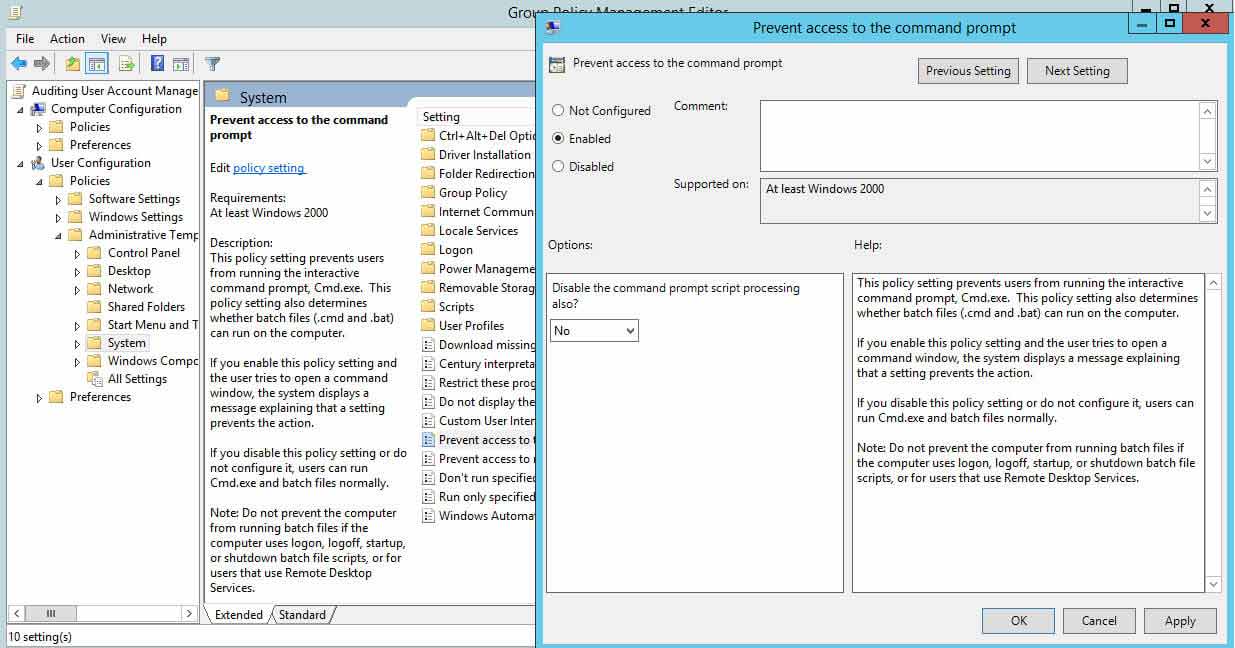 Figure 3: Prevent access to the control prompt window
Figure 3: Prevent access to the control prompt window
four. Disable Forced System Restarts
Forced system restarts are common. For instance, you lot may face up a situation where y'all were working on your computer and Windows displays a message stating that your organisation needs to restart considering of a security update.
In many cases, if y'all fail to notice the message or take some time to respond, the computer restarts automatically, and you lose of import, unsaved work. To disable forced restart through GPO, perform the post-obit steps:
- In "Group Policy Management Editor" window (opened for a custom GPO), go to "Calculator Configuration" "Administrative Templates" "Windows Component" "Windows Update".
- In the right pane, double-click "No car-restart with logged on users for scheduled automatic updates installations" policy.
- Click "Enabled" to enable the policy.
- Click "Utilize" and "OK".
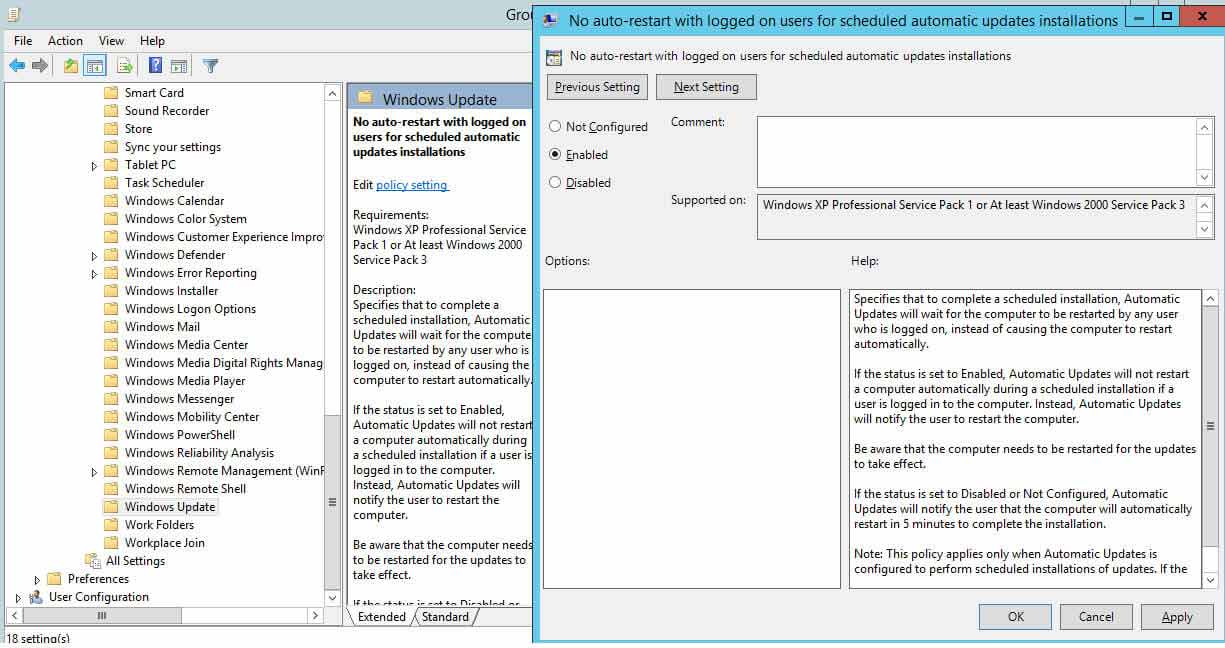 Effigy iv: No system auto-restart with logged on users
Effigy iv: No system auto-restart with logged on users
5. Disallow Removable Media Drives, DVDs, CDs, and Floppy Drives
Removable media drives are very prone to infection, and they may as well contain a virus or malware. If a user plugs an infected drive to a network computer, information technology tin can affect the entire network. Similarly, DVDs, CDs and Floppy Drives are prone to infection.
Information technology is therefore best to disable all these drives entirely. Perform the following steps to do so:
- In Grouping Policy Management Editor window (opened for a custom GPO), go to "User Configuration" "Policies" "Authoritative Templates" "System" "Removable Storage Admission".
- In the correct pane, double-click "All removable storage classes: Deny all accesses" policy
- Click "Enabled" to enable the policy.
- Click "Apply" and "OK".
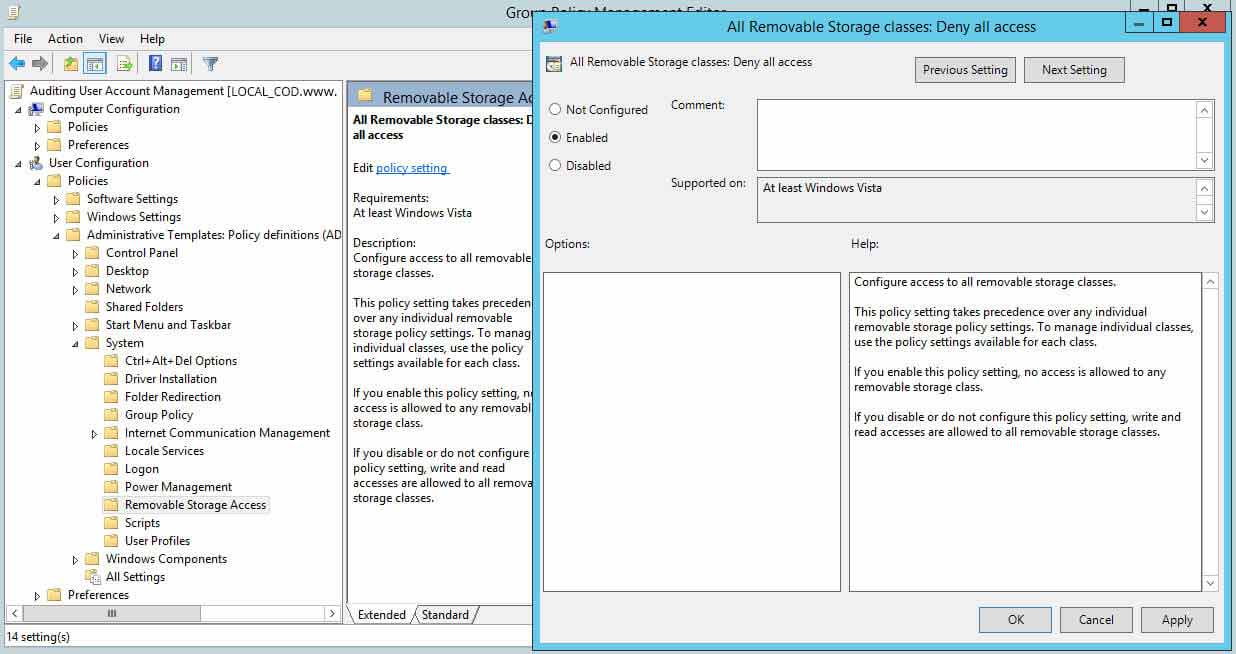 Figure five: Deny access to all removable storage classes
Figure five: Deny access to all removable storage classes
half-dozen. Restrict Software Installations
When you requite users the freedom to install software, they may install unwanted apps that compromise your organisation. System admins will usually have to routinely do maintenance and cleaning of such systems. To be on the safe side, information technology'southward advisable to forestall software installations through Group Policy:
- In Group Policy Management Editor (opened for a custom GPO), get to "Computer Configuration" "Authoritative Templates" "Windows Component" "Windows Installer".
- In the right pane, double-click "Prohibit User Install" policy.
- Click "Enabled" to enable the policy
- Click "Employ" and "OK".
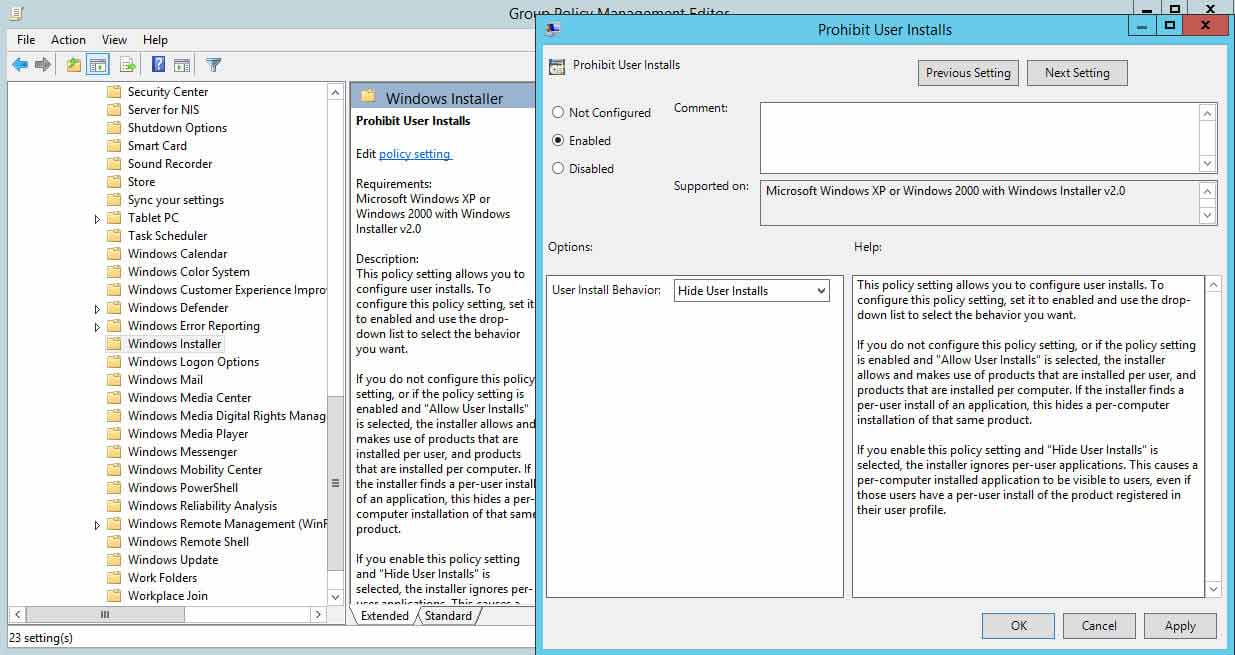 Figure 6: Restricting software installations
Figure 6: Restricting software installations
7. Disable Guest Account
Through a Guest Account, users can get access to sensitive data. Such accounts grant access to a Windows computer and do non require a password. Enabling this account means anyone can misuse and corruption access to your systems.
Thankfully, these accounts are disabled by default. It'due south best to cheque that this is the example in your It environment as, if this account is enabled in your domain, disabling it volition prevent people from abusing access:
- In Group Policy Management Editor (opened for a custom GPO), go to "Computer Configuration" "Windows Settings" "Security Settings" "Local Policies" "Security Options".
- In the correct pane, double-click "Accounts: Guest Business relationship Condition" policy.
- Select "Define this policy setting" checkbox and click "Disabled".
- Click "Utilise" and "OK".
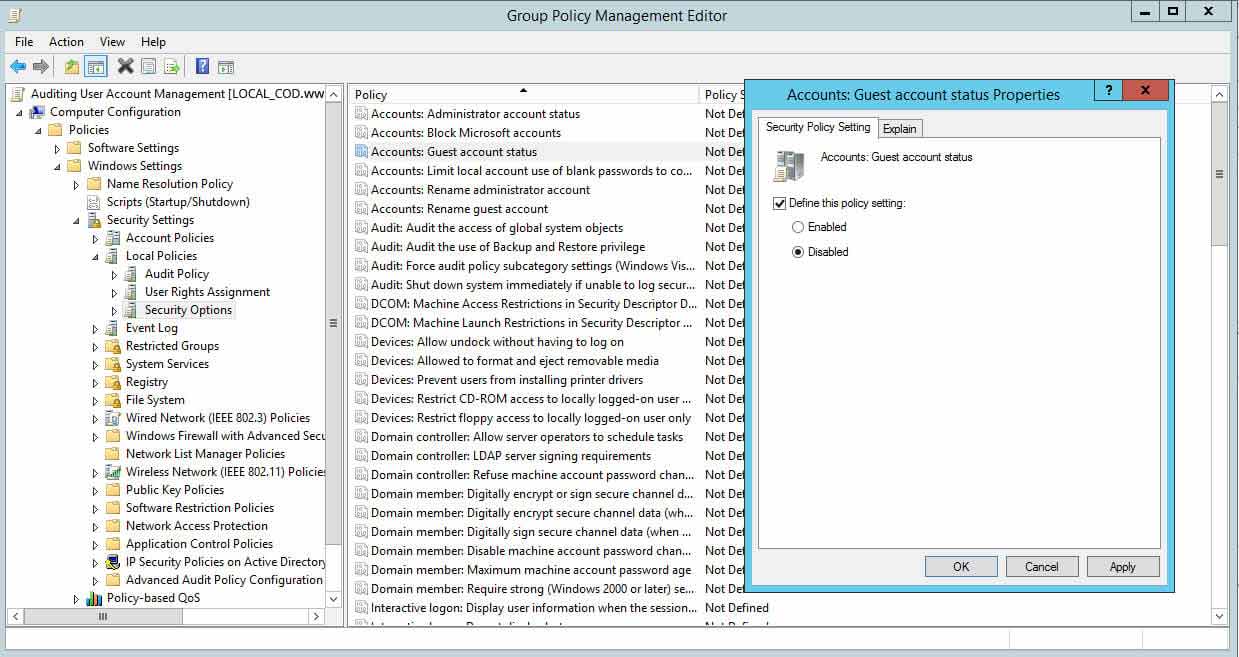 Figure 7: Disabling guest account
Figure 7: Disabling guest account
viii. Gear up Minimum Countersign Length to Higher Limits
Set the minimum password length to higher limits. For example, for elevated accounts, passwords should be ready to at least fifteen characters, and for regular accounts at least 12 characters. Setting a lower value for minimum countersign length creates unnecessary take chances. The default setting is "zero" characters, so you will take to specify a number:
- In Group Policy Management Editor window (opened for a custom GPO), go to "Computer Configuration" "Windows Settings" "Security Settings" "Account Policies" "Countersign Policy".
- In the right pane, double-click "Minimum password length" policy, select "Ascertain this policy setting" checkbox.
- Specify a value for the countersign length.
- Click "Utilize" and "OK".
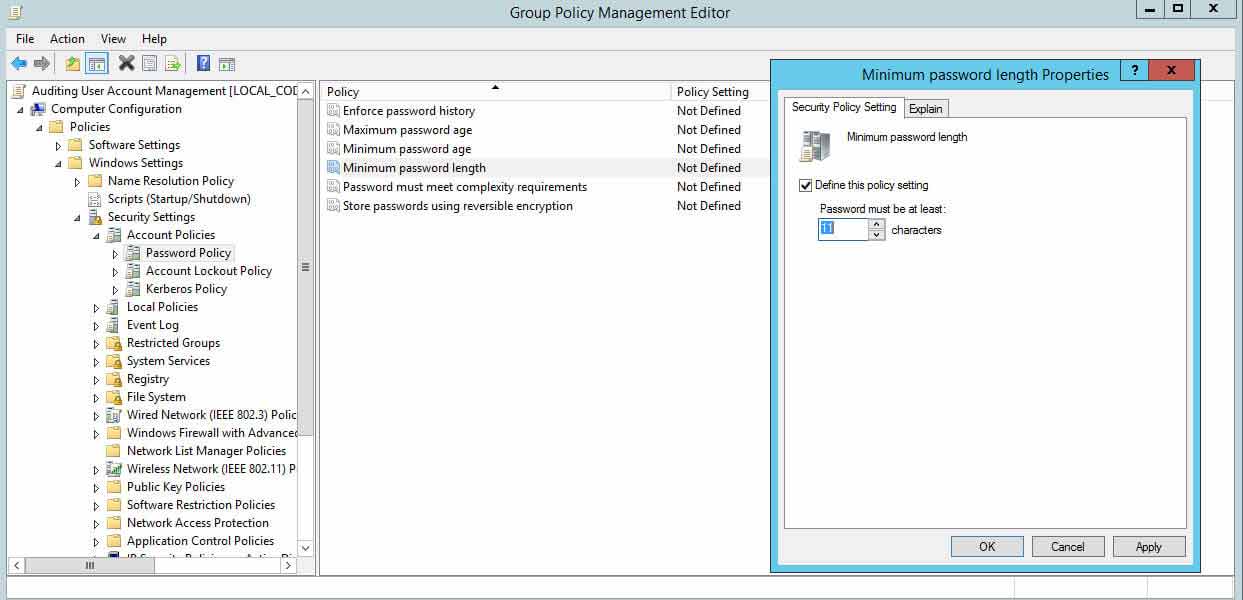 Figure 8: Configuring minimum password age policy setting
Figure 8: Configuring minimum password age policy setting
9. Set Maximum Password Age to Lower Limits
If you set the password expiration age to a lengthy menstruum of time, users will non have to change it very oft, which ways information technology's more likely a countersign could get stolen. Shorter password expiration periods are always preferred.
Windows' default maximum password age is set to 42 days. The following screenshot shows the policy setting used for configuring "Maximum Password Historic period". Perform the following steps:
- In Group Policy Management Editor window (opened for a custom GPO), become to "Figurer Configuration" "Windows Settings" "Security Settings" "Account Policies" "Password Policy".
- In the right pane, double-click "Maximum password age" policy.
- Select "Ascertain this policy setting" checkbox and specify a value.
- Click "Utilize" and "OK".
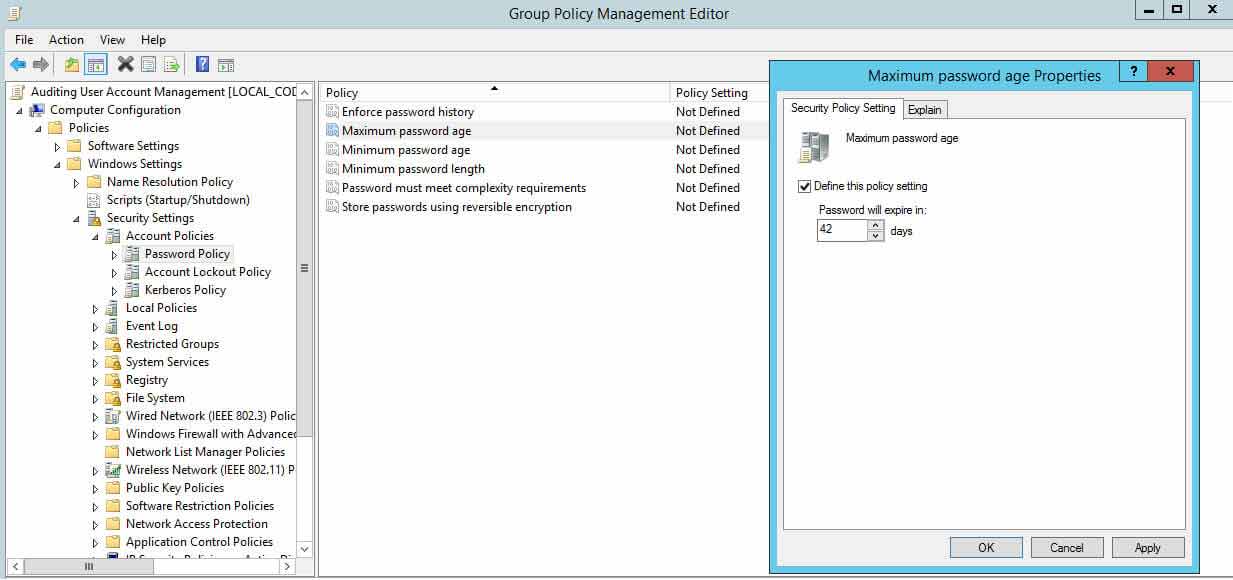 Figure 9: Configuring maximum password historic period policy setting
Figure 9: Configuring maximum password historic period policy setting
10. Disable Bearding SID Enumeration
Active Directory assigns a unique number to all security objects in Active Directory; including Users, Groups and others, called Security Identifiers (SID) numbers. In older Windows versions, users could query the SIDs to identify important users and groups. This provision can be exploited by hackers to get unauthorized access to data. By default, this setting is disabled, ensure that it remains that style. Perform the following steps:
- In Group Policy Management Editor window, go to "Computer Configuration" "Policies" "Windows Settings" "Security Settings" "Local Policies" "Security Options".
- In the right pane, double-click "Network Admission: Practice not allow anonymous enumeration of SAM accounts and shares" policy setting.
- Choose 'Enabled' and and then click 'Apply' and 'OK' to save your settings.
If you lot go these Group Policy settings correct, your organization's security volition automatically be in a improve country. Please make sure to apply the modified Group Policy Object to everyone and update the Grouping Policies to reflect them on all domain controllers in your environment.
How to Continue Group Policy Changes in Control
If you want to remain in full control of your IT Infrastructure, you lot take to make sure no unwanted changes in these policies and other Group Policies are made. You can do this past performing continuous Group Policy Object auditing.
Still, doing through native auditing tin be tricky, due to the amount of dissonance generated and the unavailability of predefined reports. To keep a continuous runway of changes made in Group Policy Objects, try Lepide Group Policy Auditor. Our solution allows yous to inspect every alter made to Group Policies in real time. Start your Free Trial today.
Source: https://www.lepide.com/blog/top-10-most-important-group-policy-settings-for-preventing-security-breaches/
Posted by: clevengerheaden.blogspot.com

0 Response to "How To Open Computer Configuration In Windows Server 2016"
Post a Comment